Six Nations 2013 what are France's chances – video Sport guardian.co.uk
Updated: 2013-01-30 18:41:55
: Turn autoplay off Turn autoplay on Please activate cookies in order to turn autoplay off Jump to content s Jump to comments c Jump to site navigation 0 Jump to search 4 Terms and conditions 8 Edition : UK US Sign in Mobile Your profile Your details Your comments Your clippings Your lists Sign out Mobile About us About us Contact us Press office Guardian Print Centre Guardian readers' editor Observer readers' editor Terms of service Privacy policy Advertising guide Digital archive Digital edition Guardian Weekly Buy Guardian and Observer photos Today's paper The Guardian G2 features Comment and debate Editorials , letters and corrections Obituaries Other lives Sport SocietyGuardian Subscribe Subscribe Subscribe to the Guardian iPhone app iPad edition Kindle Extra Guardian Weekly Digital

 While reviewing the 2013 changes to HIPAA, we came upon this interesting bit of economic impact analysis early in the document. A table is presented called “Estimated Costs of the Final Rule”. Within this table, an estimated cost is presented for Security Rule Compliance by Business Associates, expected to apply to between 200,000 and 400,000 business [...]
While reviewing the 2013 changes to HIPAA, we came upon this interesting bit of economic impact analysis early in the document. A table is presented called “Estimated Costs of the Final Rule”. Within this table, an estimated cost is presented for Security Rule Compliance by Business Associates, expected to apply to between 200,000 and 400,000 business [...] Chester talks to Paul Ducklin in Sophos Security Chet Chat Episode 101.
Spend an enjoyable quarter-hour as our duo take on a range of security issues with their usual mixture of insight, expertise, scepticism, advice and occasional outright puzzlement.
Chester talks to Paul Ducklin in Sophos Security Chet Chat Episode 101.
Spend an enjoyable quarter-hour as our duo take on a range of security issues with their usual mixture of insight, expertise, scepticism, advice and occasional outright puzzlement. What if your security camera were an insecurity camera?
Paul Ducklin investigates and offers some advice...
What if your security camera were an insecurity camera?
Paul Ducklin investigates and offers some advice... Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 690 Corporate 192 Enterprise 646 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 688 Corporate 192 Enterprise 645 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 688 Corporate 192 Enterprise 645 McAfee Labs 1095 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee People often think they don’t need to worry about security because they have nothing of value to an attacker. In October Brian Krebs posted an updated chart on the value of a hacked computer. The Indian is reported to have used every part of the buffalo, letting none of it go to waste. While not ...Continue reading ‘You are the target’ »
People often think they don’t need to worry about security because they have nothing of value to an attacker. In October Brian Krebs posted an updated chart on the value of a hacked computer. The Indian is reported to have used every part of the buffalo, letting none of it go to waste. While not ...Continue reading ‘You are the target’ » Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 686 Corporate 189 Enterprise 644 McAfee Labs 1094 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 686 Corporate 189 Enterprise 644 McAfee Labs 1094 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Corporate Blogs Corporate Responsibility 32 CTO 35 EMEA President’s View 19 McAfee Channel 100 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Corporate Blogs Corporate Responsibility 32 CTO 35 EMEA President’s View 19 McAfee Channel 100 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise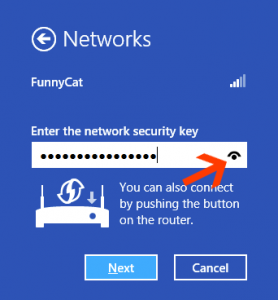 Two weeks ago, I finally got a chance to try out a Windows 8 system. First, I have to give huge kudos to Dell, who makes the XPS 12 system I’m playing with. This system seems to be the ideal platform for a Windows 8 user. A thin and light notebook with plenty of power, [...]
Two weeks ago, I finally got a chance to try out a Windows 8 system. First, I have to give huge kudos to Dell, who makes the XPS 12 system I’m playing with. This system seems to be the ideal platform for a Windows 8 user. A thin and light notebook with plenty of power, [...] The term “black swan event” was introduced by Nassim Nicholas Taleb in the book Fooled By Randomness. Black swan events have three major characteristics: they are rare, they cause a significant or extreme impact, and upon retrospection, they are actually predictable. As described very well in this Wired article, “getting hacked” is a black swan event. While “getting hacked” can mean many [...]
The term “black swan event” was introduced by Nassim Nicholas Taleb in the book Fooled By Randomness. Black swan events have three major characteristics: they are rare, they cause a significant or extreme impact, and upon retrospection, they are actually predictable. As described very well in this Wired article, “getting hacked” is a black swan event. While “getting hacked” can mean many [...] Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 682 Corporate 187 Enterprise 640 McAfee Labs 1092 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee
Skip over navigation McAfee® Blog Central Corporate Corporate Responsibility CTO EMEA President’s View McAfee Channel McAfee Labs Enterprise Cloud Security Critical Infrastructure Protection CSO Risk Management Data Center Data Protection Database Security Embedded Healthcare Management Mobile Network Security Public Sector Risk Compliance SaaS Security Connected Security Perspectives SIEM SMB Support System Endpoint Virtualization Consumer Consumer Threat Alerts Consumer Threat Notices Cyber Security Mom Cyber Security Mum Australia Cyber Security Mum India eCommerce Family Safety Identity Theft Mobile Consumer Robert Siciliano Blogs Archive 31 Consumer 682 Corporate 187 Enterprise 640 McAfee Labs 1092 Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee